What Is Dmg Servers In Network
If you have a home or work network set up for your Windows PC, you may also be mapping network shares to drive letters. Mapped drives are very convenient as they allow accessing network files and folders just like a regular local drive. Sometimes in Windows 10, mapped drives do not always automatically and reliably reconnect at logon. Let us see how to fix this issue.
RECOMMENDED: Click here to fix Windows errors and optimize system performance
If a mapped network drive wasn't reconnected, any program that tries to access resources on the mapped network drive fails.
When you create a mapped network drive, there is an option 'Reconnect at logon' which you can check so that every time Windows logs on, they are automatically mounted using the current user's logon credentials.
If you check 'Connect using different credentials', then you can specify a different user name and password.
The problem: When Windows 10 logs on, there is a timing issue which causes it to attempt to map the network drives before the network is available. This results in them being unavailable sometimes. If you press Refresh in Windows Explorer or double click the drive, they instantly become available.
To fix the issue Windows 10 Does Not Reconnect Mapped Network Drives, you need to do the following.
- Paste the following text inside Notepad and save as a *.cmd file.
Replace the domainnameusername portion with the appropriate values.
- In Notepad, press Ctrl + S or execute the File - Save item from the File menu. This will open the Save dialog. There, type or copy-paste the name 'reconnect.cmd' including quotes. Double quotes are important to ensure that the file will get the '*.cmd' extension and not *.cmd.txt. You can save the file to any desired location.
- Move the *.cmd file you created to the Startup folder. Refer to the following article: How to add or remove startup apps in Windows 10. In short, press Win + R shortcut keys together and type the following into the Run box:
This will open your Startup folder in File Explorer.
Xcode 4.4 download dmg windows 10. Aug 11, 2018 Xcode is the software development suite for Mac that allows developers to build apps for MacOS, iOS, tvOS, and watchOS. The vast majority of developers and Xcode users will download the Xcode application suite from the Mac App Store, but that’s not the only option available to download Xcode, and if you’d rather download Xcode as a DMG or XIP file directly from Apple, then those options. Where does the Mac App Store download the files to under Lion? I need the DMG file in order to repair something in my system, but how can I access that file?
- Move the reconnect.cmd file there and you are done.
That's it. Many thanks to our reader 'Jezze' for sharing this tip.
RECOMMENDED: Click here to fix Windows errors and optimize system performance
- The diagram above shows the network established using MORI-NET Global Edition Advance, the software that enables an advanced remote maintenance service or downloading of data from the servers inside DMG MORI through an Internet connection.
- Seamless control of servers running Mac OS X Server. Admin Tools uses a GUI for ease of configuration. The 10.6.4 version can administer servers running both 10.5 and 10.6 versions of the Apple.
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network or screened subnet) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted, usually larger, network such as the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN): an external network node can access only what is exposed in the DMZ, while the rest of the organization's network is firewalled. The DMZ functions as a small, isolated network positioned between the Internet and the private network and, if its design is effective, allows the organization extra time to detect and address breaches before they would further penetrate into the internal networks.
Nov 19, 2016 【METIN2】〖HACK〗x1000 DMG Hack for PServer kius1337. Unsubscribe from kius1337? Global Mountain Bike Network Recommended for you. Language: English Location: United States.
The name is from the term 'demilitarized zone', an area between states in which military operations are not permitted.
Rationale[edit]
The DMZ is seen as not belonging to either party bordering it. This metaphor applies to the computing use as the DMZ acts as a gateway to the public Internet. It is neither as secure as the internal network, nor as insecure as the public internet.
In this case, the hosts most vulnerable to attack are those that provide services to users outside of the local area network, such as e-mail, Web and Domain Name System (DNS) servers. Because of the increased potential of these hosts suffering an attack, they are placed into this specific subnetwork in order to protect the rest of the network should any of them become compromised.
Hosts in the DMZ are permitted to have only limited connectivity to specific hosts in the internal network, as the content of DMZ is not as secure as the internal network. Similarly, communication between hosts in the DMZ and to the external network is also restricted to make the DMZ more secure than the Internet and suitable for housing these special purpose services. This allows hosts in the DMZ to communicate with both the internal and external network, while an intervening firewall controls the traffic between the DMZ servers and the internal network clients, and another firewall would perform some level of control to protect the DMZ from the external network.
A DMZ configuration provides additional security from external attacks, but it typically has no bearing on internal attacks such as sniffing communication via a packet analyzer or spoofing such as e-mail spoofing.
It is also sometimes good practice to configure a separate Classified Militarized Zone (CMZ),[1] a highly monitored militarized zone comprising mostly Web servers (and similar servers that interface to the external world i.e. the Internet) that are not in the DMZ but contain sensitive information about accessing servers within LAN (like database servers). In such architecture, the DMZ usually has the application firewall and the FTP while the CMZ hosts the Web servers. (The database servers could be in the CMZ, in the LAN, or in a separate VLAN altogether.)
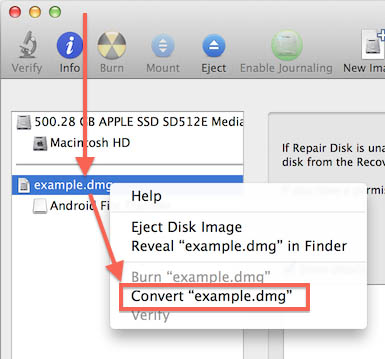 Dec 10, 2018 Creating a bootable DVD from DMG in Windows is easy, but you need special software to do the job. These two methods utilize third-party utilities to make bootable DVD using a DMG file. This quick instruction will help any-one to make a Bootable MacOS Catalina Installer.ISO and.DMG images in MacOS and Windows. MacOS Catalina.ISO is needed for installing Catalina into a virtual machine using VMWare and Virtual box and other purposes. DMG files are very common on the MacOS X platform, used for Disk Images.With Disk Images we mean a full “copy” image of for example a CD, DVD or Harddisk. DMG‘s are typically used to distribute applications. Some times however you’d prefer a ISO or a CDR image instead, for example for users on different platforms, or for offering other ways to burn an image to CD or DVD (if applicable). TransMac - Make DMG File Bootable USB on Windows. This is a fairly robust application for creating bootable USB on Windows from a DMG file. However, there's a preparatory step to be executed before you can create the bootable USB drive.
Dec 10, 2018 Creating a bootable DVD from DMG in Windows is easy, but you need special software to do the job. These two methods utilize third-party utilities to make bootable DVD using a DMG file. This quick instruction will help any-one to make a Bootable MacOS Catalina Installer.ISO and.DMG images in MacOS and Windows. MacOS Catalina.ISO is needed for installing Catalina into a virtual machine using VMWare and Virtual box and other purposes. DMG files are very common on the MacOS X platform, used for Disk Images.With Disk Images we mean a full “copy” image of for example a CD, DVD or Harddisk. DMG‘s are typically used to distribute applications. Some times however you’d prefer a ISO or a CDR image instead, for example for users on different platforms, or for offering other ways to burn an image to CD or DVD (if applicable). TransMac - Make DMG File Bootable USB on Windows. This is a fairly robust application for creating bootable USB on Windows from a DMG file. However, there's a preparatory step to be executed before you can create the bootable USB drive.
Any service that is being provided to users on the external network can be placed in the DMZ. The most common of these services are:
- VoIP servers
Web servers that communicate with an internal database require access to a database server, which may not be publicly accessible and may contain sensitive information. The web servers can communicate with database servers either directly or through an application firewall for security reasons.
E-mail messages and particularly the user database are confidential, so they are typically stored on servers that cannot be accessed from the Internet (at least not in an insecure manner), but can be accessed from email servers that are exposed to the Internet.
What Is Dmg Servers In Network Windows 7

The mail server inside the DMZ passes incoming mail to the secured/internal mail servers. It also handles outgoing mail.
For security, compliance with legal standards such as HIPAA, and monitoring reasons, in a business environment, some enterprises install a proxy server within the DMZ. This has the following benefits:
- Obliges internal users (usually employees) to use the proxy server for Internet access.
- Reduced Internet access bandwidth requirements since some web content may be cached by the proxy server.
- Simplifies recording and monitoring of user activities.
- Centralized web content filtering.
A reverse proxy server, like a proxy server, is an intermediary, but is used the other way around. Instead of providing a service to internal users wanting to access an external network, it provides indirect access for an external network (usually the Internet) to internal resources.For example, a back office application access, such as an email system, could be provided to external users (to read emails while outside the company) but the remote user would not have direct access to their email server (only the reverse proxy server can physically access the internal email server). This is an extra layer of security particularly recommended when internal resources need to be accessed from the outside, but it's worth noting this design still allows remote (and potentially malicious) users to talk to the internal resources with the help of the proxy. Since the proxy functions as a relay between the non-trusted network and the internal resource: it may also forward malicious traffic (e.g. application level exploits) towards the internal network; therefore the proxy's attack detection and filtering capabilities are crucial in preventing external attackers from exploiting vulnerabilities present in the internal resources that are exposed via the proxy. Usually such a reverse proxy mechanism is provided by using an application layer firewall that focuses on the specific shape and contents of the traffic rather than just controlling access to specific TCP and UDP ports (as a packet filter firewall would do), but a reverse proxy is usually not a good substitute for a well thought out DMZ design as it has to rely on continuous signature updates for updated attack vectors.
Architecture[edit]
What Is Dmg Servers In Network System
There are many different ways to design a network with a DMZ. Two of the most basic methods are with a single firewall, also known as the three legged model, and with dual firewalls, also known as back to back. These architectures can be expanded to create very complex architectures depending on the network requirements.
Single firewall[edit]
A single firewall with at least 3 network interfaces can be used to create a network architecture containing a DMZ. The external network is formed from the ISP to the firewall on the first network interface, the internal network is formed from the second network interface, and the DMZ is formed from the third network interface. The firewall becomes a single point of failure for the network and must be able to handle all of the traffic going to the DMZ as well as the internal network.The zones are usually marked with colors -for example, purple for LAN, green for DMZ, red for Internet (with often another color used for wireless zones).
Dual firewall[edit]
The most secure approach, according to Colton Fralick,[2] is to use two firewalls to create a DMZ. The first firewall (also called the 'front-end' or 'perimeter'[3] firewall) must be configured to allow traffic destined to the DMZ only. The second firewall (also called 'back-end' or 'internal' firewall) only allows traffic to the DMZ from the internal network.
This setup is considered[2] more secure since two devices would need to be compromised. There is even more protection if the two firewalls are provided by two different vendors, because it makes it less likely that both devices suffer from the same security vulnerabilities. For example a security hole found to exist in one vendor's system is less likely to occur in the other one. One of the drawbacks of this architecture is that it's more costly, both to purchase, and to manage.[4] The practice of using different firewalls from different vendors is sometimes described as a component of a 'defense in depth'[5] security strategy.
DMZ host[edit]
Some home routers refer to a DMZ host, which—in many cases—is actually a misnomer. A home router DMZ host is a single address (e.g., IP address) on the internal network that has all traffic sent to it which is not otherwise forwarded to other LAN hosts. By definition, this is not a true DMZ (demilitarized zone), since the router alone does not separate the host from the internal network. That is, the DMZ host is able to connect to other hosts on the internal network, whereas hosts within a real DMZ are prevented from connecting with the internal network by a firewall that separates them unless the firewall permits the connection.
A firewall may allow this if a host on the internal network first requests a connection to the host within the DMZ. The DMZ host provides none of the security advantages that a subnet provides and is often used as an easy method of forwarding all ports to another firewall / NAT device. This tactic (establishing a DMZ host) is also used with systems which do not interact properly with normal firewalling rules or NAT. This can be because no forwarding rule can be formulated ahead of time (varying TCP or UDP port numbers for example, as opposed to a fixed number or fixed range). This is also used for network protocols for which the router has no programming to handle (6in4 or GRE tunnels are prototypical examples).
See also[edit]
- Science DMZ Network Architecture DMZ for high performance computing
References[edit]
- ^Bradley Mitchell (27 August 2018). 'Demilitarized Zone in Computer Networking'. Retrieved 10 December 2018.
- ^ abJacobs, Stuart (2015). Engineering Information Security: The Application of Systems Engineering Concepts to Achieve Information Assurance. John Wiley & Sons. p. 296. ISBN9781119101604.
- ^'Perimeter Firewall Design'. Microsoft Security TechCenter. Microsoft Corporation. Retrieved 14 October 2013.
- ^Zeltzer, Lenny (April, 2002). 'Firewall Deployment for Multitier Applications'
- ^Young, Scott (2001). 'Designing a DMZ'. SANS Institute. p. 2. Retrieved 11 December 2015.
Non-standard / no citation template[edit]
- SolutionBase: Strengthen network defenses by using a DMZ by Deb Shinder at TechRepublic.
- Eric Maiwald. Network Security: A Beginner's Guide. Second Edition. McGraw-Hill/Osborne, 2003.
- Internet Firewalls: Frequently Asked Questions, compiled by Matt Curtin, Marcus Ranum and Paul Robertson